Adding security headers to prevent XSS and MiTM attacks in .Net Core
As a developer, we need to consider security when designing and building web applications. HTTP Response Headers allow server to pass additional information to instruct browsers how to handle sensitive data and content of the application and/or from external or untrusted sources. HTTP response security headers provide an extra layer of protection to help mitigating vulnerabilities and attacks.
One way to add those security headers from .Net Core application is by writing a custom action filter that would be executed before serving any response from the application.
Below is a example of the custom attribute:
To apply this globally for all responses, we can add this to the Startup class as in below:
To apply trusted source for any particular action:
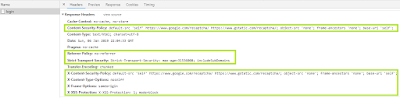
And here is the outcome:
HAPPY CODING 👌
One way to add those security headers from .Net Core application is by writing a custom action filter that would be executed before serving any response from the application.
Below is a example of the custom attribute:
To apply this globally for all responses, we can add this to the Startup class as in below:
To apply trusted source for any particular action:
And here is the outcome:
HAPPY CODING 👌

security headers
ReplyDelete